Network Security Monitoring
6 Lessons Learned from Recent Cloud Security Breaches
September 29, 2021
7 minutes

Recent cloud security breaches have prompted a large degree of uncertainty in the business world—driven largely by several crucial factors; namely increasingly sophisticated cyberattack vectors, susceptibility among SMBs, and working circumstances that arose because of the onset of the pandemic.
Since the COVID pandemic began and through 2020 and 2021, there has been a drastic uptick in cyberattacks against both businesses and users, many of which have been driven simply as a result of the remote work environment and the difficulties organizations have had in properly securing their employees’ devices away from the office.
What should be most concerning, however, is the impact that this is having on small and midsize businesses in particular.
Sign up for our newsletter!
While it’s certainly true that enterprise organizations are targeted in the biggest and most costly data breaches, the sheer volume of smaller attacks—typically through social engineering—that are today targeting SMBs is cause for great concern.
Around half (47%) of all cyberattacks are directed at SMBs.
When you further consider how uniquely pre-disposed SMBs are to attacks—owing to a common lack of effective cybersecurity strategies and tools—we now have a situation in which IT executives and decision makers should be paying close attention to what they can do to reduce their risk of succumbing to a breach.
With breaches often proving fatal to SMBs and a common modern cause of bankruptcy, it’s crucial to learn from breaches and avoid them.
Today, we’re going to take a look at some significant breaches in recent years and discuss six lessons that can be learned from them.
1. Take a Top-down Approach
Large data breaches in the last few years have brought the issue of cybersecurity to the forefront for business leaders.
In 2017, 150 million people had their personal information compromised in the Equifax breach—something that proved to have long-term ramifications for the company (a global settlement that included $425 million of support for those affected was only finalized in 2020).
The Equifax breach came at a time when larger scrutiny was being put on the protection of personal records and individuals whose data is stored by organizations.
In 2018, the number of personal records exposed in data breaches increased by 126% compared to 2017 when the Equifax breach occurred.
More worryingly, however, is that between 2020 and 2019 there was an increase of 66% in exposed records, suggesting the volume of incidents is continuing to grow at a concerning rate.
As the incidence of attacks rise, it’s becoming clearer that executive decision making will be key to driving better plans for cybersecurity to ensure buy-in at all levels and improve the security profiles of businesses.
While in 2019, just 54% of executives were knowledgeable and engaged in their company’s responses to breaches, in 2020 89% of organizations had clarified security roles and responsibilities within their executive team, suggesting a marked improvement in responses to security risks.
Having executives and decision makers directly involved in cybersecurity policies and strategies (as opposed to just IT) is essential in heading off modern threats, and businesses should take a top-down approach with their IT security.
2. Educate Your Employees
The fact of the matter is that when cyber breaches happen, the chances are it’s because an employee has fallen victim to a cybercriminal.
It’s estimated that 90% of all cyberattacks can be attributed in some way to human error.
This is because hackers and cybercriminals operate off of the basis of seeking the path of least resistance—in other words, when it comes to malware, it’s distributed indiscriminately and those who fall victim are more likely to be the unprepared rather than the unfortunate.
Businesses that prepare their workforce and educate them on best practices on how to avoid becoming the victim of a breach (and a point of entry for hackers into the organization) have a much better standing when it comes to preventing cybercrime.
This is why DOT Security offer security awareness training to clients—because it’s a key component in a modern cybersecurity strategy.
Nearly half of all breaches of data are caused directly by employee negligence, such as the loss of a device or sharing sensitive information where it shouldn’t be online by accident.
Improving the awareness of a workforce means addressing common bad habit regarding data hygiene and ensuring they can handle sensitive information without the risk of it being stolen or falling into the wrong hands.
Employee education has proven enormously effective—for organizations that use security awareness training, 79% avoided a breach, compared to 69% who didn’t adopt any training.
3. Manage IoT Devices Correctly
The Internet of Things, or IoT, environment has had an enormous impact on the IT infrastructure of businesses all over the world.
The nature of cybersecurity is often that businesses are often in a reactive state of mind—traditionally cyberattacks have had to occur for cyber professionals to know what to protect against. This is changing a lot because of new technologies like AI and machine learning being introduced into cybersecurity strategies, but nevertheless remains a key point.
The dramatic growth of IoT technology within organizations over the last 10 years has led to a sharp increase in the number of devices that exist within modern business networks.
More devices means more endpoints, and more endpoints means more entryways for hackers into networks.
In fact, because of the greater vulnerabilities that exist now because of the rise of IoT, nearly half of all SMBs have experience at least one data breach related to IoT—this should be cause for great concern.
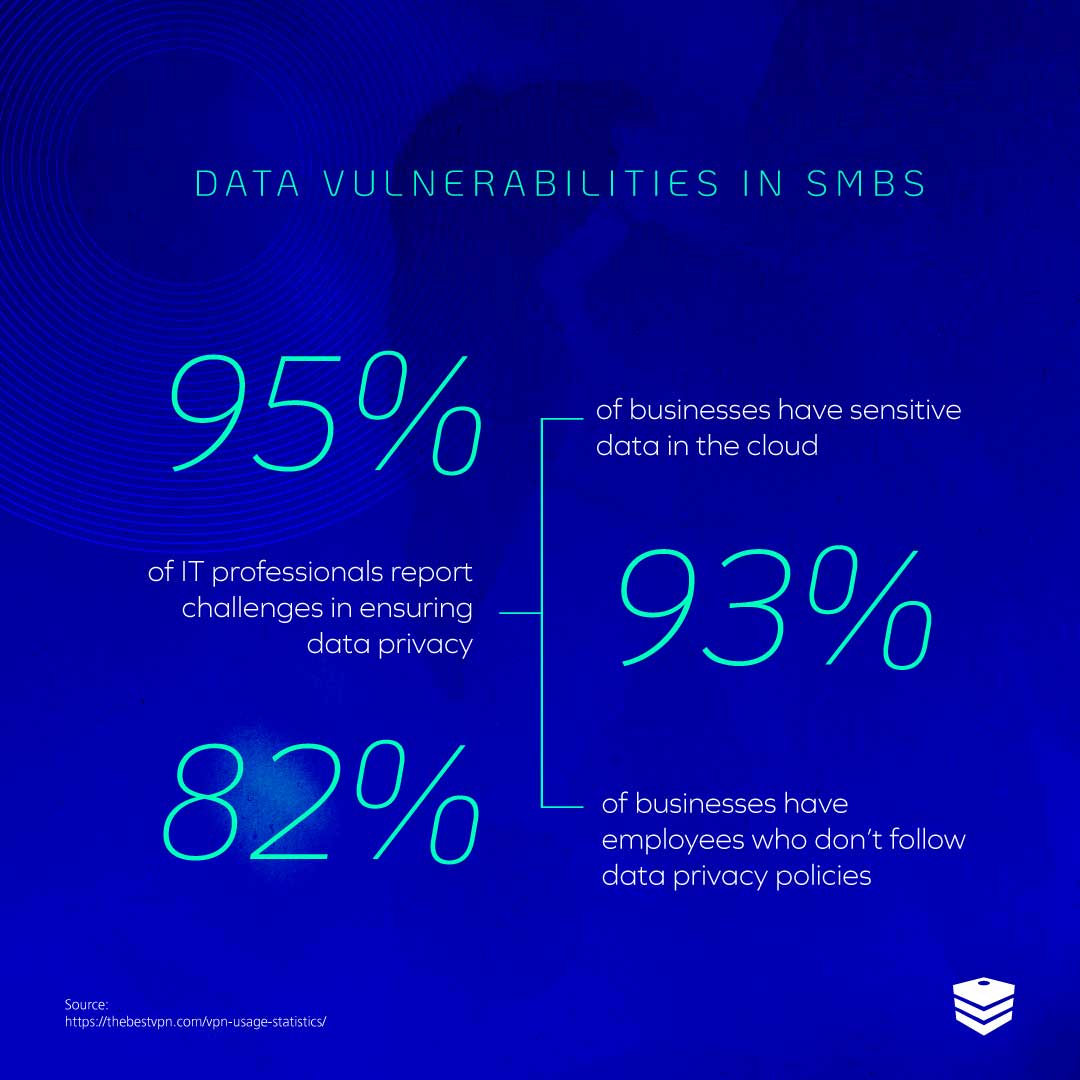
With around 95% of employees stating they use at least one self-purchased device for work (typically using them to connect to the office network to do so), businesses cannot be confident that every device under network is secured.
Because of this, it’s vital for companies to be sure that they are protecting the data through enforcing security tools at the network level.
For many, this means the implementation of a comprehensive cloud security mobile device management platform. With an MDM, security professionals can ensure that every device under network is correctly monitored and maintained on a more granular level than previously possible.
4. Prepare for Disaster Recovery
One crucial lesson from data breaches that should be learned is the importance of a quick recovery.
This is because many data breaches simply go unnoticed by businesses.
The average time of data breach discovery is 279 days—over nine months.
When cybercriminals are smart, they will often try to leave the company unawares by methodically siphoning data over a long period of time.
The longer the lifecycle of a breach, the more lasting damage that occurs to the business.
In addition, when there is a catastrophic breach that causes downtime for the company, every minute of business operations lost is money and opportunity lost, before even getting into the recovery of compromised information.
For these reasons, not only is it important to root out irregularities in the network, but also to recognize that the quick operations and information is restored and back to normal, the better.
A disaster recovery and business continuity plan is crucial to achieve this and should focus on a few key things:
- Image-based cloud backups of installed OSs on network devices
- Regular (time determined by the business’ specific RTO and RPO) saved images that can be restored quickly
- A communication plan in place so everybody in the chain of command knows what their job is in the event of a breach
These things can be achieved quite realistically for the vast majority of businesses with the cybersecurity solutions of today.
Most modern data centers offer Tier III or IV servers which offer excellent standards for downtime and have the capacity to get an organization up and running in no time.

5. Cybersecurity Is Ongoing, Long-term
Cybersecurity is not a one-and-done solution.
IT environments in businesses can change significantly over years and even months—companies’ needs change, their infrastructure shrinks and grows; more devices are provisioned; more employees are onboarded.
The situations of SMBs are always in flux, and for this reason a cybersecurity strategy that was a good fit for one year maybe outdated the next.
Many businesses utilize the services of a consultant—often a virtual Chief Information Officer (vCIO)—in order to make sure their plans are up to date and remaining on the right track.
DOT Security recommends regular reports, often quarterly or bi-annual, which can include risk audits, to ensure the current needs of the business are being met.
This also goes for compliance standards, which are often changing, being brought into new regulations, and affecting new companies.
In short, cybersecurity changes constantly, and so understanding that needs change is critical to ensuring a strategy that is comprehensive and relevant.
Don’t let your strategy become outdated and vulnerable through idleness.
6. Invest In Your Cybersecurity
Investment in cybersecurity is higher today than it has ever been.
In 2021, spending on cybersecurity surpassed $150 billion, an increase of 12% over 2020, which itself had seen growth of 6% over 2019.
The reason for this greater investment in cybersecurity is because of a growing recognition among business owners and IT executives about the pressing need to ensure that their organizations remain safe as network environments become more uncertain.
If businesses are uncertain about where they stand with regards to their cybersecurity practices, policies, and solutions, it’s a good idea to have a managed security service provider conduct a risk assessment to determine what they need to do next to shore up their security capabilities.
