Endpoint Protection
Network Security Vulnerabilities to Watch Out For
December 08, 2021
4 minutes

To secure your network security vulnerabilities, you need to know what and where they are.
With multiple devices, remote access, cloud-based storage, and more now being used consistently in the workplace, it’s time to start thinking about your network’s security vulnerabilities and how you can secure them.
Sign up for our newsletter!
What is a Network Security Vulnerability?
A network security vulnerability is any form of weakness within a business’ system, including software, hardware, processes, or protocols, which could be compromised by a cyber threat and result in a security breach and potentially the loss of data, money, and reputation.
Common Network Security Vulnerabilities for Businesses
These vulnerabilities come in a few different forms and are typically the result of poor training and upkeep of cybersecurity systems. Here are a few of the most common examples of network security vulnerabilities.

Malware
Malware is malicious software that, when installed onto your system, can cause damage in a number of different ways, depending on which form of malware you are the victim of. Some typical forms of malware are:
• Viruses: When a virus is installed onto your computer, it quickly replicates itself, usually without the knowledge of the user, and they can even spread from one computer to another. They can cause havoc on your network and steal critical data.
• Ransomware: This malware locks you out of your system, denying access until a “ransom” is paid.
• Spyware: This software installs itself discreetly onto your computer and tracks your habits and collects data which can be sold to third parties.
• Keyloggers: Also known as “keyboard capturing”, keyloggers track a user’s keystrokes and sends that data to hackers. This is a common way to steal passwords, credit card information, and other sensitive data.
Malware gets into your system in many ways, also. They can be hiding in email attachments, pop ups, downloads, software, and almost anywhere else on the web. Malware can steal your information, spy on your actions, affect the performance of your computer, and much more.
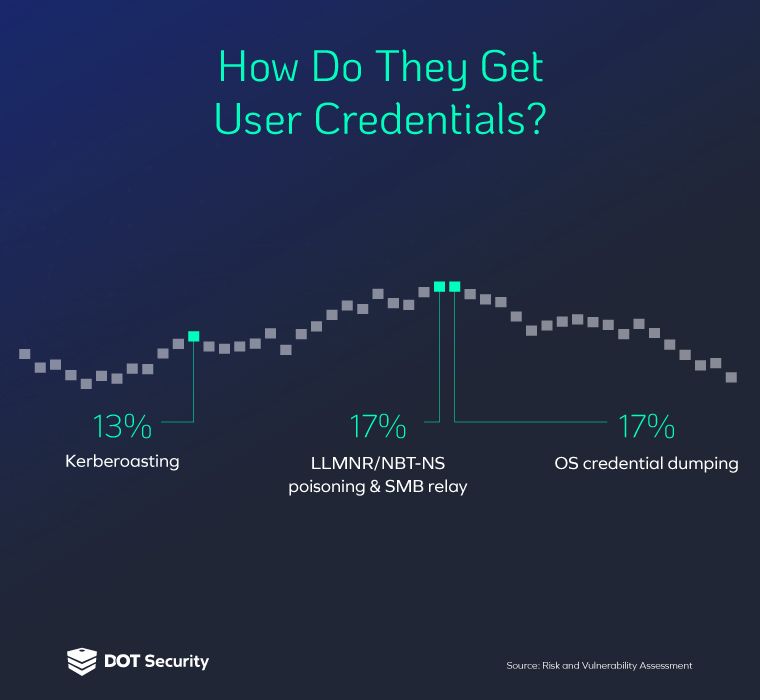
User Error or Lack of Education
One of the biggest vulnerabilities a company can have is an uniformed workforce who lacks knowledge of basic cybersecurity best practices and doesn’t know what to look for in order to avoid scams like phishing.
Sometimes known as “social engineering attacks,” these are aimed at normal employees and are most commonly found in the form of a phishing email which is designed to deceive and trick people into willingly giving up sensitive information, clicking malicious links, or opening attachments.
49% of cyber criminals who get access to a private network get it from people who click links within a phishing email.
The reason this works so often and so well is the lack of proper cybersecurity education being given to employees. A better-informed staff is a more secure one.
Outdated Software
Software applications, especially large ones like operating systems, are made up of thousands to millions of lines of code, meaning that vulnerabilities are almost certain.
Developers are constantly releasing updated patches to fix bugs, reduce errors, remove vulnerabilities, and increase performance.
That’s why it’s so important to keep all your software updated to ensure that all of it is running at its peak performance and isn’t under threat from old holes in security.
Misconfigured Firewalls and Software
Using the internet in business brings some inherent risks, that’s why we enlist the help of security measures like firewalls which act as the first line of defense between your internal network the internet.
A firewall monitors traffic going in and out and decides whether or not to allow it based on a set of security protocols.
A poorly configured firewall will allow traffic into your network that shouldn’t be there and which poses a risk. Bad actors can easily take advantage of weak firewalls to launch cyber attacks and steal information.
Be sure to run consistent penetration testing to test the effectiveness of your cybersecurity threat prevention, like firewalls, to make sure they’re updated and working to deter malicious traffic.
Unsecured Endpoints
Another common way cyber criminals can find their way into your network is via an insecure device.
This can mean a lot of things, but typically comes from employees using devices like laptops, tablets, and phones with weak passwords, un-updated software, or by connecting these devices to insecure networks like coffee shop Wi-Fi.
This has become a larger problem with the growing number of remote workers who use their own devices and work from anywhere, connecting to many different networks in the process.
To help, educate your workforce in cybersecurity best practices and make sure your organization has strong cybersecurity protocols for password creation, access management, multi-factor authentication, and device management in order to be as secure as possible.
How to Secure Your Vulnerabilities
If your business uses the internet in your business practices, then you have network security vulnerabilities that need to be addressed with proper protection like cybersecurity education, firewalls, access management, and device security.
The first step to doing this is a network security audit from an experienced managed security service provider like DOT Security. We start by assessing your current situation, discovering vulnerabilities, then we design a strategy that’s customized to meet your business needs and deploy it with long-term management and updates.
Want to learn more about how a security audit from DOT Security can help you discover your business’ vulnerabilities and build a strategy to cover them up? Contact us today to speak with an expert about how you can get started.
