Cybersecurity Consulting
Infographic: The Layered Cybersecurity Defense
October 03, 2023
6 minute read

The most effective cybersecurity strategy is a layered one. This involves deploying multiple levels of security controls to protect against all types of cyberattack, eliminate single points of failure in your network security, and minimize the chance of a data breach.
In this blog, we’ll discuss the layers included in a comprehensive cybersecurity strategy and their role in the overall defense of a network.
Sign up for our newsletter!
If you want a better understanding of your current posture and where you might improve your network’s security, you can review DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
The 7 Layers of Cybersecurity
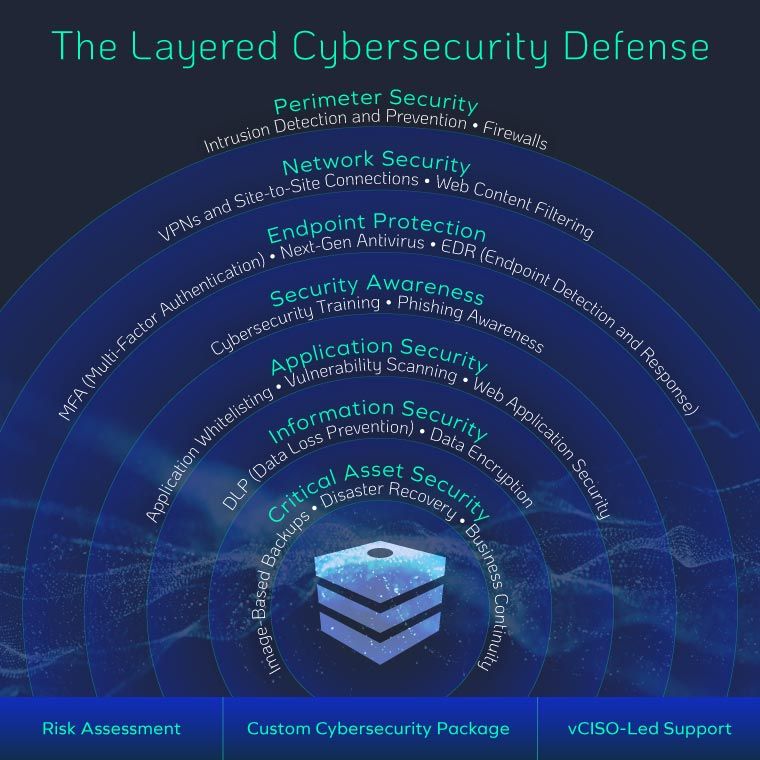
1. Perimeter Security
Perimeter security solutions protect data between a private internal network and an external public-facing network.
In short, it’s a protective shield for your business, fending off threats that come from the outside.
Traditionally, perimeter security has been the epitome of cybersecurity insofar as network security was concerned. Once upon a time, it was often sufficient for companies to use just a perimeter firewall solution.
While a modern layered cybersecurity approach is much broader in nature, perimeter security still plays a vital role in securing data internally for businesses.
There are several solutions that play into perimeter security; most notably, unified threat management and web application firewalls.
Unified threat management is an excellent way to uncover and nullify potential threats attempting to breach your network. It’s an umbrella technology including software like firewalls, antivirus, intrusion protection, spam filtering, content filtering, and in some cases, VPN support for encrypted communications.
A web application firewall, or WAF, is similar, but focuses on data traveling between the end user and the cloud app they’re using. Because so many businesses today store, handle, and access data in the cloud, WAFs have become vital to comprehensive cybersecurity strategies.
2. Network Security Monitoring
Monitoring tools provide total visibility into your network and help identify unusual activity and vulnerabilities.
These tools include vulnerability scanning, security information and event management (SIEM), and network detection and response (NDR).
Vulnerability scanners use machine learning to automatically assess risks associated with functions and processes across your hybrid network—whether in the cloud or internally. When vulnerabilities are detected, they are prioritized in terms of their threat level and patched to ensure safety.
SIEM is a monitoring and event management solution that can be integrated with several major tech providers like Microsoft. This solution will alert you if it recognizes something like a suspicious login, excessive failed login attempts, or other instances of abnormal behavior across your network.
Implementing security information and event management effectively creates a centralized database of any and all threats and abnormalities identified and escalates them to your IT team in real time for remediation when necessary.
Network detection and response (NDR) is similar, but is more focused on network traffic analysis (NTA), detecting anomalies, and providing more granular data on security events that raise suspicion.
NDR solutions help businesses increase network visibility, offering a more extensive approach to threat detection than SIEM alone.
3. Security Awareness and Employee Training
Cybersecurity awareness and training is one of the most important, yet underrated, aspects of a comprehensive cybersecurity strategy.
Employee manipulation and social engineering is the most common way threat actors breach a network. Cybersecurity awareness training empowers employees to identify and report these types of scams without compromising the network.
Ongoing cybersecurity awareness training is vital because there are always new scams hitting the malware market. Pig butchering scams, for instance, only just started grabbing media attention in early 2023.
Investing in a cybersecurity awareness program is an excellent way to safeguard a business and will become a necessity as cybercriminals continue to rely heavily on social engineering as a primary attack vector going forward.
4. Endpoint Protection
Just as WAFs (web application firewalls) are more significant now because of the increased use of cloud apps in organizations, endpoint protection is also now more important because of the modern prevalence of the Internet of Things (IoT) and operational technology. In turn, this has led to a substantial increase in the number of devices businesses have to protect and vulnerabilities for which they need to account.
Endpoints are everywhere in a modern business environment—smart monitors, mobile devices, printers, vending machines, thermostats—you name it.
In 2015, there were 15 billion Internet-connected devices worldwide. In 2020, that figure had doubled to 30 billion—by 2025 it will be 75 billion.
To manage these endpoints, businesses should use domain name system (DNS) protection. A good way to think about DNS is as an address book, only with IP addresses instead of physical ones.
By identifying different IP addresses, DNS protection stops access to malicious sites and can be extended to all devices under a network. This means an employee browsing on their phone over your company network won’t accidentally end up on a malicious website that compromises your network.
“70% of attacks involve the DNS layer in some way. Attacks are either launched via deceptive sites or websites are used in malware exploits.”
Then we have managed detection and response (MDR), which is an endpoint protection service that detects, prevents, and responds to attacks across all vectors.
As opposed to searching for the characteristics of malware, which can be hidden or morphed into something unrecognizable, MDR monitors the processes of every endpoint, recognizing deviations from the norm and responding to those abnormalities.
Finally, we have persistence detection. “Persistence” refers to a modern hacking process whereby cybercriminals gain access to your systems and wait for the opportune moment to strike, lingering silently in the background undetected.
This solution uses advanced technology to sniff out bad actors hiding in plain sight by collecting information and activity associated with persistence mechanisms that evade other cybersecurity technologies.
5. Information Security
Information security is all about limiting access and stopping inadvertent data loss. Data loss prevention (DLP) is all about preventing data leakage, which refers to the unauthorized transfer of data from inside your organization to outside.
DLP aims to rectify this issue by establishing clear standards for your data storage and handling through labeling and categorizing. This means determining where certain data should be stored, who has access to it, and where it can be shared.
The identity access management approach is a standard best practice in cybersecurity programs and helps avoid the significant issues that data leakage can bring to a business.
Email protection, meanwhile, operates on the same premise, only for your email communications. Email protection solutions help prevent many common attacks like phishing, spam, and malware communicated to end users through email servers.
6. Authentication Protocols
Authentication solutions ensure the people accessing your business data are who they say they are. Identity authentication is a simple and effective way of preventing unauthorized users from accessing your business data.
In fact, Microsoft estimates that something as simple as using multi-factor authentication (MFA) stops 99% of all automated brute force attacks.
MFA, which requires the use of a secondary device or method to authenticate a user, has proven especially useful in preventing breaches as users must provide multiple forms of unique identification. Additionally, it’s worth noting that there are several strong MFA applications that are fairly easy to integrate.
Likewise, automated password management solutions help ensure your employees are consistently updating their passwords with formidable credentials that won’t easily be breached.
Multi-factor authentication and password management tech work together to give you and your staff an edge in network defense and cybersecurity posture.
7. Critical Asset Security
In case of data disaster, businesses need to retrieve lost information as soon as they possibly can, otherwise the cost of downtime may be too great for them to overcome.
Backup and disaster recovery (BDR) services are aimed at making sure that any vulnerable information in your business, whether it’s data stored on internal servers, external cloud data, or website data, is backed up and can be restored instantly.
Last on this list, we have software-as-a-service backup, which protects the data that people handle on their cloud applications, as well as website data backup, which restores all data from your website in the event of a breach. Recovering this data promptly is integral to returning operations to 100% in the wake of a breach.
Wrapping Up on Layered Cybersecurity
A layered cybersecurity defense is a critical approach for organizations to protect their networks and data from cyberthreats. By implementing all seven of the security layers covered in this piece, organizations can ensure that their networks and data are protected from multiple angles, reducing the risk of successful cyberattacks.
However, organizations should note that a layered cybersecurity defense is not a one-time solution. It requires regular monitoring, ongoing assessment, and continual improvement to stay effective in the face of evolving cyberthreats.
Get an idea of where your cybersecurity posture is today by reviewing DOT Security’s Cybersecurity Checklist: How Covered is Your Business?
