Identity And Access Management
Identity and Access Management (IAM) Standards
March 28, 2024
8 minute read

Identity and access management (IAM) standards are business processes and policies designed to manage access to information and systems. As such, IAM plays a crucial role in keeping networks safe and secure.
IAM standards create an environment in which only authorized users can get the data they need to do their jobs. Making sure that users can only access the data they actually need is also known as the principle of least privilege.
Sign up for our newsletter!!
On the flip side of this coin, identity and access management standards prohibit unauthorized users from gaining access to your data or sensitive information. Implementing these standards will also make it much harder for a malicious actor to get their hands on data even in the event of a breac.
Current businesses have many employees sharing data or accessing it from both inside and outside the network. They also face numerous external threats to their systems. IAM standards ensure that the data is protected and only accessed by authorized individuals.
If you’re looking for identity and access management solutions, visit our IAM offerings page to explore about how DOT Security's enterprise access management.
Identity and Access Management (IAM) Framework
The Identity Management Institute recommends all organizations follow the AAA (Authentication, Authorization, and Accounting) IAM framework in order to manage user access and company assets, and to maintain account security.
By following the AAA framework, institutions can better protect themselves against modern, sophisticated cyberattacks.
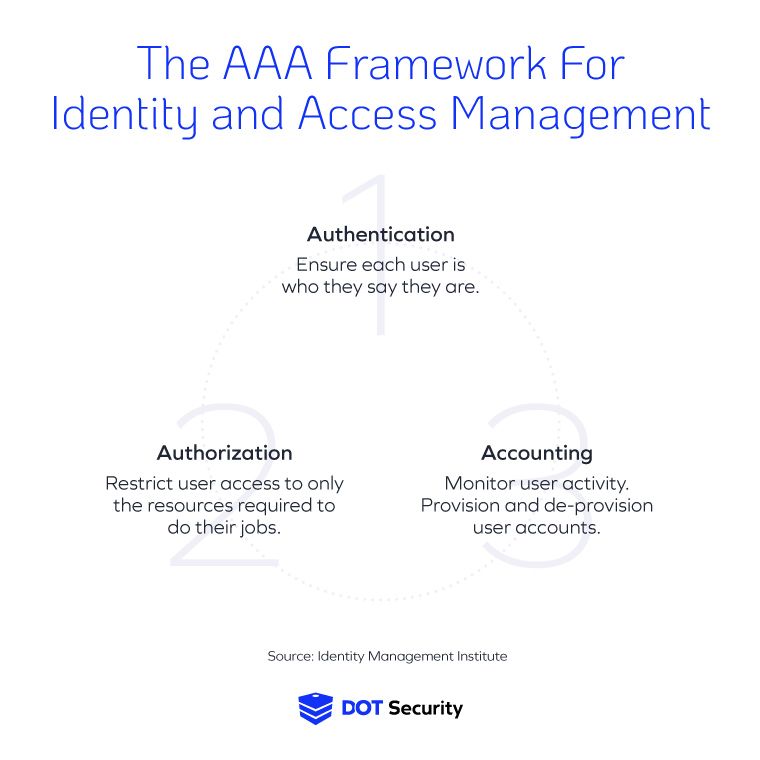
Here’s a closer look at the three pillars of the AAA framework for IAM aimed at protecting your data:
1. Authentication
Authentication is the process of ensuring each user is who they say they are. For example, to enter a place that serves alcohol, people produce drivers’ licenses or photo IDs that can prove they are of age. Using someone else’s ID would get you blocked from the bar.
Similarly, for your company accounts, no two employees should share the same credentials. This allows administrators to clearly audit user data if the need arises and allows them to better help users troubleshoot problems with accounts.
User authentication can be verified with the following methods:
- Something you know: A username or a password.
- Something you have: A device or an authenticator app.
- Something you are: A biometric such as a fingerprint or voice.
DOT Security recommends everyone in your organization use MFA (multi-factor authentication) which is a combination of at least two of the methods mentioned above. For instance, a user would enter their login name and password, and then authenticate their identity with an authenticator app or a code sent to their device.
Using an MFA can prevent over 99% of cyberattacks compromising accounts according to Microsoft.
Strong passwords can be a sturdy shield to protect your organization, but there are ways to make sure that they’re even stronger. By creating a comprehensive password policy within your organization, you ensure that users are creating passwords of a certain caliber.
A great tip for creating strong passwords is to use passphrases instead.
2. Authorization
Authorization is the second A in the AAA framework. In simple terms, it means giving users authorization to only the accounts and data they need to perform their jobs. This is also what data segmentation and the policy of least privilege are designed to do; restrict employees' access to the data and information they specifically need.
The principle of least privilege states that users, devices, processes, and programs should only have access to what is required to do their jobs. In other words, not all users should have access to all the sensitive and valuable data on the network. This means instilling an organizational hierarchy of users with various levels of privilege such as administrators, managers, users, viewers, etc.
The principle of least privilege is a vital part of a strong cybersecurity posture considering about 20% of confirmed data breaches were caused by internal actors. Having a hierarchy of user access will help prevent accidental or intentional cybersecurity violations such as sharing of data to unauthorized people or deleting important information.
3. Accounting
The last A of the AAA framework stands for accounting or auditing. Accounting means monitoring user activity within the network. Conducting regular audits of different user accounts will prevent suspicious activity going unnoticed and allows the organization to determine whether users have the correct level of access.
Accounting should also cover the provision and de-provision of accounts. For instance, whenever employees are onboarded, the company would have a protocol to give them the necessary account access. When an employee leaves, the offboarding process should include removing account access.
Auditing accounts is important to prevent data extraction from disgruntled employees or other malicious activities.
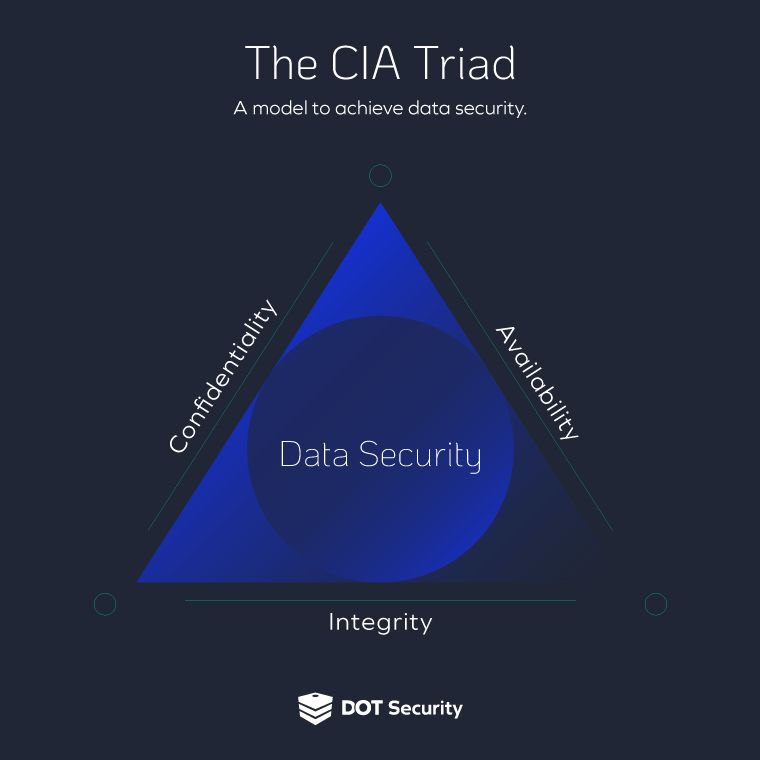
These three pillars of the AAA IAM framework will help your business protect the confidentiality, integrity, and availability of your data. Also known as the CIA triad, this framework for safeguarding data is one of the most fundamental cybersecurity standards.
System and Network Monitoring
In addition to the AAA model, another cybersecurity standard best practice is rooted in network monitoring.
System and network monitoring sort of acts as a safety net when it comes to identity and access management standards because it gives your IT and cybersecurity professionals more visibility into network activities. With this additional information readily available, your security experts can watch out for suspicious activities and anomalies across the network.
If a specific event or activity is flagged, it can then be further investigated and appropriately categorized as a false-positive or a verified threat. If the threat is verified, your team can jump into an incident response and remediation plan to effectively isolate, neutralize, and then learn from the breach.
Effective network monitoring plays a crucial role in maintaining the security posture of an organization's IT infrastructure by providing real-time visibility into network activities, enabling prompt incident response, and ensuring compliance with security policies and regulatory requirements.
In the context of IAM, network monitoring also helps organizations enforce access controls and authentication mechanisms by monitoring user activities, detecting suspicious login attempts, and identifying potential insider threats or unauthorized access to sensitive resources.
By continuously monitoring network traffic and user activities, organizations can proactively identify and address security vulnerabilities, safeguard their digital assets, and protect against cyber threats.
IAM Standards and Compliance
Depending on your industry, your business may be required to adhere to different compliance laws and regulations. Privacy laws such as the GDPR, HIPAA, CCPA, and others require your business to protect consumer data and privacy.
For example, the HIPAA Privacy Rule requires organizations to block employee access to PHI (protected health information) as soon as the employee leaves the organization or is terminated.
Similarly, the GDPR and CCPA laws require businesses to maintain access management and strong authentication methods to protect data related to their customers.
Therefore, an IAM standard such as the AAA framework detailed above will ensure customer data is protected and confidential.
Following compliance regulations will not only prevent fines and legal penalties, but will also ensure your business benefits from long-term customer trust, which directly affects your business reputation, brand identity, and potential for growth.
Companies that implement identity and access management standards like the AAA framework will meet the required compliance standards and reduce the risk of a data breach or cyberattack.
Wrapping up on Identity and Access Management Standards
In today’s cybersecurity environment, where SMBs are being targeted just as frequently as larger enterprises, and where those same SMBs often lack the necessary security protocols, the identity and access management standards outlined by the AAA framework will ensure that networks and systems are adequately protected.
Don’t leave identity and access security up to error-prone, manual processes. Use standards like those found in IAM frameworks like the AAA to get your access control measures modernized and to put your strategy for data protection on the right track.
DOT Security’s goal is to help organizations mature their cybersecurity strategy and implement modern industry best practices. Learn about our identity and access management (IAM) solutions to protect your company accounts and data.
