Secure Data Protection
How to Measure Cybersecurity Risk in a Business
November 09, 2023
6 minutes

With the increasing number of cyber incidents, many organizations are starting to recognize that they need to invest more into their cybersecurity posture. Measuring cybersecurity risk is a vital step in the assessment and preparation stage when deciding on your cybersecurity solutions.
By measuring your cybersecurity risk, you’ll gain an idea of where your current cybersecurity posture stands, where there are glaring gaps in your defense, and which solutions will provide the most immediate benefit.
Sign up for our newsletter!
Read on to learn about the steps you can take to identify your risks, assess your vulnerabilities, and prepare to secure them with a holistic cybersecurity strategy.
If you’d first like to find out how the DOT Security team takes a deep dive to find all business network vulnerabilities, check out the blog The DOT Security Risk Audit.
What is Cybersecurity Risk?
Cybersecurity risk represents the potential that organizational data is lost or compromised. Specifically, cybersecurity risk is associated with the business's technological infrastructure.
This is important to measure and understand because a successful cyberattack against can cause more than a one-time monetary loss: it can create ongoing reduced sales, reduced trust, and even downtime or closure.
Different organizations will have varying levels of cybersecurity risk based on any number of variables. For example, the type and amount of data they collect, the industry in which they operate, and even the region in which they operate can all impact the level of cybersecurity risk an organization carries.
Ways to Measure a Business’ Cybersecurity Risk
Though it’s not an exact science, there are a few ways to measure and understand a business’ cybersecurity risk.
Here are a few things that can help you know where your vulnerabilities are and how susceptible you may be to an attack.
1. Benchmark Programs Against Competitors
One of the most effective ways to measure your cybersecurity stature is to compare your system to those of your competitors and peers within your industry.
Seeing the cybersecurity performance of other companies can help you make a more informed decision on what your biggest weaknesses are and what you need to do to fix them.
The industry you belong to will also dictate in some way how much cyber risk your business carries. For example, governmental agencies and industries like finance, energy, and healthcare are frequently targeted by phishing campaigns and other cyberattacks launched by criminals.
For organizations in these industries, and really all modern businesses, a cybersecurity strategy needs to offer enough protection and anticipation that it effectively reduces the impact of a cyber incident should one occur.
2. Assess Third-Party Cybersecurity Risks
Sometimes the biggest risks to a company’s network are its third-party vendors or software's that they use or work with every day.
“Incidents involving partners tend to be substantially larger than those caused by external sources.” - Data Breach Investigations Report, Verizon
While data breaches caused by a partner are not as numerous as those deployed by outside attackers, it’s worth exploring and understanding a third party’s cybersecurity standing before using their tools or doing business with them. Especially since breaches caused by partners can bring about more damage to the victim organization.
To do this, you can send a third-party partner questionnaire on cybersecurity, determine a set of compliance requirements for your business that third parties must adhere to, and have a general understanding of the risks that come from working with third parties.
3. Monitor Cybersecurity Analytics
Sometimes the numbers will help you truly understand your cybersecurity risks and vulnerabilities. Monitoring the right metrics can clearly show you where you are most vulnerable. This is also why it can be so beneficial to have a team of cybersecurity professionals working with 24/7 monitoring technology.
Here are a few key cybersecurity metrics to track:
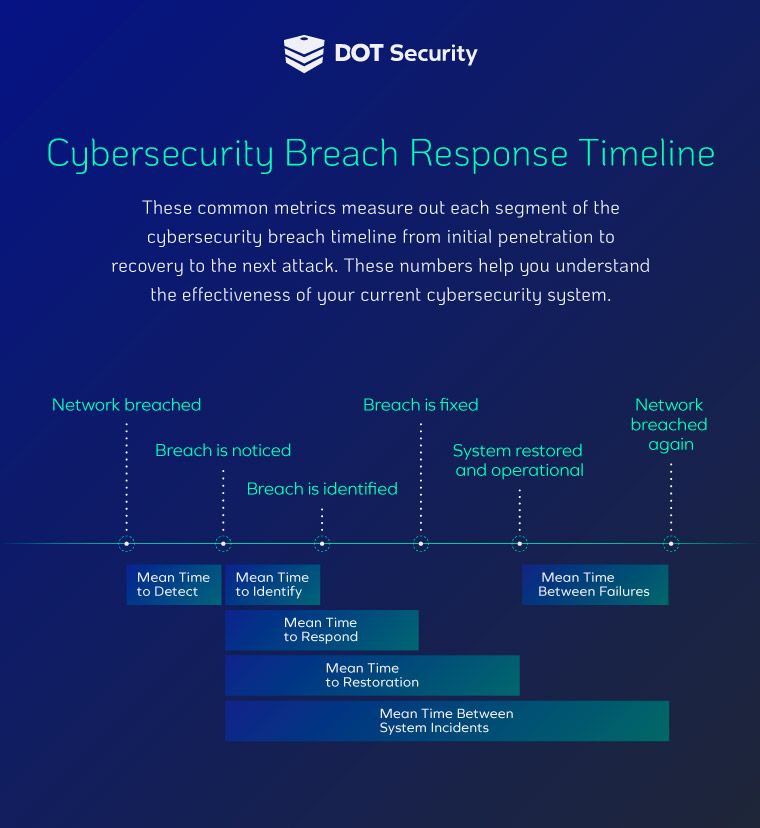
- Mean Time to Identify (MTTI) and Mean Time to Respond (MTTR): These two statistics identify how long it takes your current cybersecurity system to detect and respond to threats that enter your network. A long MTTI or MTTR can lead to higher data breach costs.
The MTTR is a direct measurement of how long some business-critical systems remain offline due to an attack. There are additional statistics set inside the breach response timeline such as mean time to repair (MTTR), mean time between failures (MTBF), mean time to failure (MTTF), mean time to restoration (MTRS), and mean time between system incidents (MTBSI).
- Data Transfer Volume: This metric gives businesses an idea of the amount of data being downloaded or how many files are uploaded. Misuse of company resources by downloading potentially dangerous files online can leave the door open for hackers, and tracking data volumes can help you identify if this is happening.
Additionally, employees may inadvertently download malicious files if they fall for a phishing scam. Phishing emails or texts are messages crafted to appear to come from legitimate sources, but trick the victim into clicking a link or downloading a file that compromises their system.
- User Access Statistics: There are a few smaller metrics to track within user access, including how many users have certain access levels and how long it takes to deactivate accounts, for example.
Not all users in your organization should have access to all data and accounts. Taking advantage of identity and access management (IAM) standards helps you ensure data and resources are available only to those who need it to do their job.
- Device Numbers: Every device on a network is a potential vulnerability if not protected. To make sure a business’ endpoints are secured, you need to know how many are in use, where they are used, and the data they’re accessing.
With the growing number of flexible work environments, endpoint security services and solutions ensure that employee devices aren’t left as an open and easy path that cybercriminals could take into your organization’s network.
4. Identify Vulnerabilities
Identifying vulnerabilities comes from a lot of internal monitoring and awareness. Examine your processes for updating software, changing passwords, managing user access, and monitoring your network to get a better idea of where your weaknesses are.
A layered cybersecurity strategy helps you identify and protect each of your assets at every level of your network. Consider reviewing the following layers to identity any potential vulnerabilities:
-
Your perimeter: Does your business use firewalls or next-gen antivirus?
-
Your endpoints: What is the level of security each device has? Do you have protection for IoT (Internet of things) and other endpoint devices that aren’t laptops or mobile phones, like sensors or manufacturing machinery?
-
Web security: Do you block malicious websites or applications?
-
Information security: Is your sensitive data encrypted whenever it is shared?
-
Critical Assets: What happens in case of a disaster or downtime? Do you have accessible backups to critical resources?
-
Cybersecurity awareness: Have you trained your employees on security best practices so they can become another layer of defense?
5. Perform a Cybersecurity Risk Audit
Part of identifying vulnerabilities can be performing a cybersecurity risk audit which dives deeper into every nook and cranny of a business’ digital environment.
There’s no better way to get a thorough understanding of where you are most vulnerable to attack.
The biggest hurdle for most companies is not knowing where to start or how to do an audit that reaches every part of the business. For example, a red team of penetration testers will use technology to examine your entire network and employ tactics such as social engineering to test your workforce on best practices.

Oftentimes, the best option is to get the help of a full-fledged team of cybersecurity experts to do it for you and report back with their findings and their solutions.
Wrapping Up on Measuring Cybersecurity Risk
Knowing and understanding your cybersecurity risk is the first step toward improving your overall cybersecurity posture. Once you know where you’re vulnerable, you know what to address and how to address it.
Building a comprehensive cybersecurity posture is necessary in today’s extremely digital world. If you need help measuring and mitigating your cybersecurity risk, consider working with a team of cybersecurity professionals who can help you integrate the right solutions for your organization.
Learn more about DOT Security’s Risk Audit Process and how we help businesses find and fix their security weaknesses here.
