Network Security Monitoring
Infographic: Evolution of Cybercrime: 5 Graphs and Charts That Show How It’s Changed
February 05, 2022
4 minutes

Cybercrime is a constantly evolving environment—new attacks and vectors rise each year and it’s crucial that businesses understand the threat posed by malware.
Malicious actors and cybersecurity professionals find themselves in a never-ending tug-of-war—constantly trying to outwit one another.
Sign up for our newsletter!
As far as organizations are concerned, it’s important for them to understand what the biggest threats are to their networks and what they can do to protect against them.
This infographic illustrates how cyberattacks have changed over the last five years, and what business decision-makers should be most aware of moving forward.
Take a look!
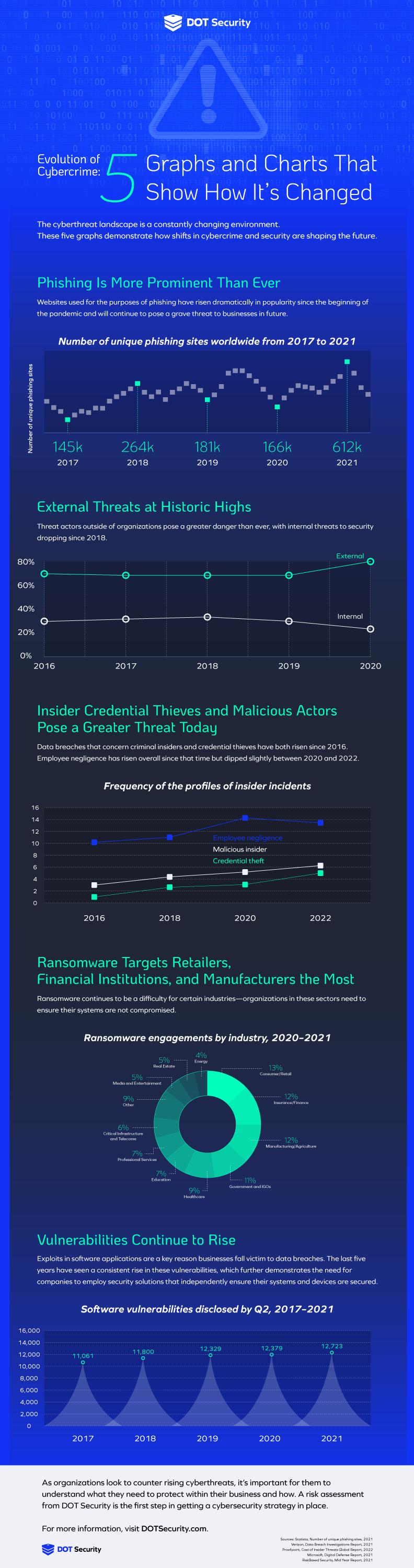
Phishing Is More Prominent Than Ever
The dreaded “P” word has been growing in significance over the 2010s, and the onset of the pandemic sped up the prevalence of these attacks by a quite astonishing rate.
Between 2017 and 2021, the number of unique phishing sites worldwide increased by 322%.
Cybercriminals who target organizations with phishing aim to use social engineering in order to persuade users to click on links, download attachments, or otherwise compromise sensitive information in some way.
In the case of the COVID pandemic, many malicious actors posed as authoritative sources for medical information in an effort to trick users into visiting their sites and sharing sensitive information.
A crucial defense against phishing is the implementation of cybersecurity awareness training programs for employees.
Security awareness training educates users on what to look out for, meaning the success of incoming phishing attacks is substantially reduced.
External Threats at Historic Highs
Attacks coming from external sources—of which phishing attacks are a good example—are today at a higher rate than they’ve ever been.
This is largely because of the rise of cyberattacks hitting businesses in general over the last few years. Cyberattackers have traditionally, and indeed still do to a large extent, targeted enterprise corporations with their malware.
Virtually all SMBs (96%) say that they will change their cybersecurity strategies due to COVID-19.
More recently, as technology adoption among SMBs has grown, hackers have increasingly sought to attack small- and medium-sized companies.
This is because of two primary reasons.
Firstly, the greater use of tech has led to a drastic increase in the volumes of data being handled by SMBs in 2022. Where there’s more data—particularly sensitive customer or employee data—there’s more opportunity for cybercriminals to exploit.
Secondly, SMBs have a tendency to lag behind when it comes to adopting the security precautions necessary to head off dangers. As a result, they often make for good targets for hackers.
The combination of these two factors means that external threats to businesses today are at the highest level they have ever been, and organizations should be weary.
For those who are unsure if they are capable of defending themselves against attack, consider having a security risk assessment conducted in order to determine what solutions and practices should be incorporated for a better defense strategy.
Credential Theft Is Rising Faster than Other Vectors
When it comes to insider threats, which make up a substantial one-fifth of all attacks, employee negligence is far and away the biggest precipitating factor in data breaches.
“Employee negligence” typically refers to the sharing, handling, or storing of data in a manner that leads to its exposure.
For example, an employee sharing sensitive information to an unsecured cloud folder which is subsequently breached.
In order to avoid this, it’s important that organizations pursue an information security (InfoSec) policy that establishes clear access controls.
A good access control policy operates under the assumption that employees only need access to the data necessary to complete their daily tasks.
It’s often the case in companies, especially SMBs, that access control policies are not in place and users have access to information they don’t need to.
By implementing proper access controls, the attack surface (probability of being breached by a cyberattack) is significantly reduced, helping organizations stay safe.
Ransomware Targets
The targets of ransomware cyberattacks are, by and large, quite evenly spread in terms of victimized industries.
Retailers, the financial industry, and manufacturers are notable for the greater number of ransomware attacks that target them.
56% of IT decision makers say that a ransomware attack on their business is either “likely” or “very likely” over the next year.
Ransomware is proving to be a big issue for many organizations that operate in critical infrastructure supply chains.
Vulnerabilities Continue to Rise
Software vulnerabilities in applications widely used by businesses are the cause of many data breaches.
These vulnerabilities have increasingly been on the rise for the last five years and indicate the need for businesses to invest in solutions that can protect them regardless of the state of third-party applications.
This can be done through the adoption of technology like endpoint protection and monitoring and threat hunting software that utilizes AI and machine learning.
Are you in need of cybersecurity services but don’t know where to start? Consider having a risk assessment done by DOT Security. Get in touch to get started today!
