Identity And Access Management
Password vs. Passphrase: Which Is More Secure?
May 02, 2024
8 minute read

Passwords are typically short single-word (around eight characters) credentials that may make use of special characters. Passphrases, on the other hand, are much longer (typically between 16-32 characters), are much easier to remember, and much more difficult for threat actors to crack.
Obviously, passphrases offer more security than passwords, but that’s not all there is to this story. The following sections will take a closer look at the differences between passwords and passphrases and delve into the nuances that make passphrases so strong.
Sign up for our newsletter !
“Instead of using a short, complex password that is hard to remember, consider using a longer passphrase.”
Federal Bureau of Investigations
If you want to stay on top of everything happening in the cybersecurity space, including top news stories, the biggest trends, and new best practices, subscribe to the DOT Security blog for updates right to your inbox.
What Is a Password?
A password is a string of characters used to verify the identity of a user who is trying to access a computer system, device, or account. Passwords are typically created by the user or auto-generated by an app and are kept confidential in order to prevent unauthorized access to sensitive resources.
In order to ensure security, passwords should be complex (including at least one special character and number), long (use at least 16 characters), unique, and changed regularly to prevent them from being guessed or hacked.
What Is a Passphrase?
A passphrase is a sequence of words, rather than just a single word, used as a security measure for authentication or encryption purposes.
Functionally, passphrases are identical to passwords in that they are kept secret and used to authenticate user access. However, passphrases tend to be longer and more complex, making them more difficult for hackers to crack, and yet, easier for valid users to remember than traditional passwords.
Unlike passwords, which are typically shorter and less straightforward, passphrases are often more user-friendly, making them a popular choice for secure authentication and encryption methods.
For example, a strong passphrase made up of four random words can look like “SillyK!ttiesL0veTre@ts!” This passphrase works because:
- It has a reference only the individual user will remember
- It is difficult to guess and will not appear in a common password database
- It uses special characters, capital and lowercase letters, and numbers
- It is longer than 16 characters
It might seem like a bad idea to use a string of words for your credentials, but passphrases are actually much easier to remember when compared to complex passwords that have no strong mental association, and still offer much better security.
Why Are Passphrases Important?
Passphrases are important because they’re an easy way to improve your cybersecurity and defend against potential attacks without having to change much about your current identity and access management system.
Simple passwords are not as secure today as they once were due to brute force attacks. However, many people still rely on them every day, often reusing the same password for multiple accounts, increasing the amount of cybersecurity risk an organization carries.
“The more a password is reused, the more opportunities there are for your data and money to be stolen. If a reused password gets leaked as part of a data breach, hackers then have the key to your other online accounts.”
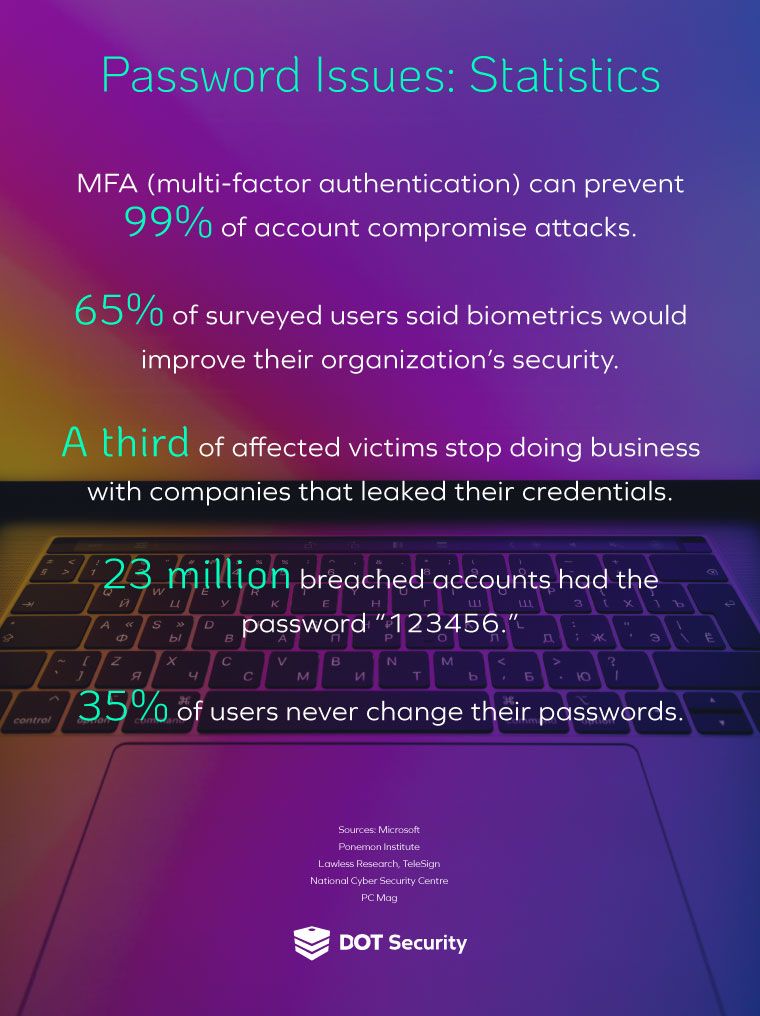
In fact, 13% of Americans use the same password for every account they own.
Simply adopting newer techniques like passphrases instead of one-word passwords is an easy way to improve your cybersecurity posture and defend against potential attacks.
Human Error and Cybersecurity
You can use every solution in the world, and it still won’t matter if someone clicks on a malicious link from a phishing campaign.
The unfortunate reality is that human error plays a critical role in successful cyberattacks. When cybercriminals perform attacks, they send out thousands (or even millions) of spam messages to dupe victims into following a malicious link. All it takes is one person to fall for their scam, which happens on an all-too-regular basis.
This means that even the strongest passwords and passphrases you cook up can be bypassed if a threat actor manages to trick someone into falling for a social engineering attack.
In fact, in late 2023, Caesars Entertainment fell victim to a massive data breach that all started with a social engineering attack against the internal IT department. A malicious actor posed as an employee in order to manipulate the IT department into handing over credentials.
Once a malicious link or file has been engaged, the hacker has a number of ways to breach the end user’s device—including tactics like installing a keylogger, directing them to a fraudulent website, or infecting the device with malware. They can then access sensitive personal or business data by logging in at will and stealing information.
This is a common way that organizations are breached and continues to be a major problem today. 52% of companies acknowledge staff as the biggest security vulnerability they need to address.
However, it’s not quite so simple as the employee being at fault. For example, even if a password is stolen, an organization that has implemented multi-factor authentication (MFA) will see the hack prevented.
The above hypothetical demonstrates the value of a layered cybersecurity defense. Implementing MFA protocols and emphasizing employee training and awareness around cybersecurity can drastically strengthen your overall security standing.
The Role of Employee Awareness and Cybersecurity Training
When it comes to account security, no password or passphrase, regardless of strength and complexity, will matter if an employee falls victim to a phishing scheme. This is because phishing scams often result in the victim directly handing over credentials to threat actors.
While passphrases will help secure accounts from a wide variety of cyberattacks, powerful passphrases need to be supplemented by proper cybersecurity awareness training.
In order to help employees avoid being duped, it’s vital that modern organizations take the time to train staff on cybersecurity awareness. These trainings can happen at various points throughout employment and, in fact, should occur on a regular cadence.
For instance, employees should undergo an initial cybersecurity awareness training at onboarding, and should engage in follow-up trainings on at least an annual basis.
By conducting regular cybersecurity awareness training for your staff, they should be able to easily identify tell-tale signs of a phishing campaign, enabling them to both avoid and report any phishing schemes that find their way into their email inbox. This is a great example of how organizations can benefit from multiple layers of cybersecurity protection.
Establishing a Password Policy
In addition to creating strong, complex, and lengthy passphrases that are easy for you to remember but nearly impossible for others to guess, and educating your staff to be cybersecurity aware; establishing a password policy adds another protective element that helps keep users safe on your network.
Password policies can range in complexity and terms but in general, they should include several key factors:
- Password update timelines
- Password length and complexity terms
- Multi-factor authentication protocols
- Password manager/password vault policies
By creating and implementing a password policy, you’ll have assurance that the passwords protecting employee accounts meet standard best-practices, offering the highest security possible.
Brute Force Attacks
When cybercriminals are looking to hack someone’s account, they don’t sit there typing in different combinations of a password for weeks on end until they guess right. Rather, they design a computer algorithm (or buy one from the dark web) to do it for them.
The algorithm will test tens of millions of combinations again and again until eventually the password is cracked.
The shorter the password, the quicker this process happens. This type of cyberattack is known as a brute-force attack and is very common today.
Over 80% of breaches caused by hacking involve brute force or the use of lost or stolen credentials.
Length is the best defense against brute force cyberattacks because it introduces exponentially more possible character combinations, making a complicated and lengthy passphrase the ideal option over a shorter password with even the most complex string of characters.
FBI Recommendation
Finally, we have the FBI’s recommendation on the use of passphrases for businesses.
The FBI launched a project called Protected Voices with the intention of providing cybersecurity recommendations to political campaigns and businesses operating in the US.
The project called for passphrases and multifactor authentication to be used to best ensure that sensitive data was protected. Passphrases were strongly advised to improve security and better protect sensitive data.
As we can see from the FBI's recommendations, passphrases are the standard best practice regarding cybersecurity and should be used by every modern organization looking to improve their security.
Wrapping up on Passphrases vs. Passwords
Many passwords and habits employed by end users are not fit for the sophistication and regularity of cyberattacks today. However, using more secure passphrases over passwords is strongly advised to tamper total cybersecurity risk.
Businesses should also strongly consider implementing MFA protocols and regular employee awareness training alongside passphrase policies to bolster their cybersecurity, prepare for potential cyberattacks, and minimize the amount of cyber risk they carry.
Stay on top of everything in the cybersecurity industry by subscribing to the DOT Security blog for regular updates on major headlines, new trends, and upcoming best practices!
